 동빈나
동빈나
|
 비전공자를 위한 이해할 수 있는 파이썬: 1시간 30분으로 파이썬 끝내기
비전공자를 위한 이해할 수 있는 파이썬: 1시간 30분으로 파이썬 끝내기
|
2024-08-31 22:07:29
|
2024-09-30 21:05:26
|
x
|
 동빈나
동빈나
|
 딥러닝 전이 학습(Transfer Learning) 완벽 이해: BiT 논문 설명 (ECCV 2020)
딥러닝 전이 학습(Transfer Learning) 완벽 이해: BiT 논문 설명 (ECCV 2020)
|
2023-03-25 23:50:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 IT 개발 회사 실전 면접 Tip 대방출: 비전공자 가상 면접 (Feat. SW마에스트로)
IT 개발 회사 실전 면접 Tip 대방출: 비전공자 가상 면접 (Feat. SW마에스트로)
|
2023-01-14 21:15:02
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 배치 정규화(Batch Normalization) [꼼꼼한 딥러닝 논문 리뷰와 코드 실습]
배치 정규화(Batch Normalization) [꼼꼼한 딥러닝 논문 리뷰와 코드 실습]
|
2021-01-14 13:45:02
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 GAN: Generative Adversarial Networks (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
GAN: Generative Adversarial Networks (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
|
2020-12-23 07:30:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
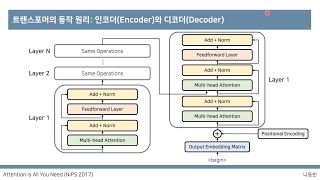 [딥러닝 기계 번역] Transformer: Attention Is All You Need (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
[딥러닝 기계 번역] Transformer: Attention Is All You Need (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
|
2020-12-13 15:49:24
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [텍스트 분류 모델 공격 기법] TextFooler: Is BERT Really Robust?
[텍스트 분류 모델 공격 기법] TextFooler: Is BERT Really Robust?
|
2020-11-23 07:07:32
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
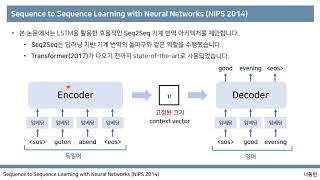 [딥러닝 기계 번역] Seq2Seq: Sequence to Sequence Learning with Neural Networks (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
[딥러닝 기계 번역] Seq2Seq: Sequence to Sequence Learning with Neural Networks (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
|
2020-11-13 07:30:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 코딩 테스트를 위한 트리(Tree) 자료구조 10분 핵심 요약
코딩 테스트를 위한 트리(Tree) 자료구조 10분 핵심 요약
|
2020-11-08 17:00:06
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 코딩 테스트를 위한 벨만 포드 알고리즘 7분 핵심 요약
코딩 테스트를 위한 벨만 포드 알고리즘 7분 핵심 요약
|
2020-11-07 14:51:49
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 자료구조: 바이너리 인덱스 트리(Binary Indexed Tree, BIT, 펜윅 트리) 10분 정복
자료구조: 바이너리 인덱스 트리(Binary Indexed Tree, BIT, 펜윅 트리) 10분 정복
|
2020-11-06 20:30:03
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 최소 공통 조상(Lowest Common Ancestor, LCA) 알고리즘 10분 정복
최소 공통 조상(Lowest Common Ancestor, LCA) 알고리즘 10분 정복
|
2020-11-05 20:02:38
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 자료구조: 우선순위 큐(Priority Queue)와 힙(Heap) 10분 핵심 요약
자료구조: 우선순위 큐(Priority Queue)와 힙(Heap) 10분 핵심 요약
|
2020-11-04 20:00:02
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 ResNet: Deep Residual Learning for Image Recognition (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
ResNet: Deep Residual Learning for Image Recognition (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
|
2020-10-29 10:44:23
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 컴퓨터 공학과를 위한 최신 논문 찾아 읽는 방법 정리 (입문자를 위한)
컴퓨터 공학과를 위한 최신 논문 찾아 읽는 방법 정리 (입문자를 위한)
|
2020-10-15 20:40:24
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
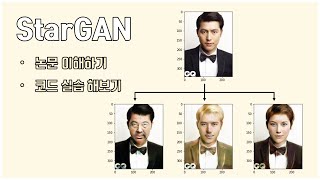 StarGAN (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
StarGAN (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
|
2020-10-13 09:12:42
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 10. 개발형 코딩 테스트
(이코테 2021 강의 몰아보기) 10. 개발형 코딩 테스트
|
2020-10-10 23:07:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 9. 코딩 테스트에서 자주 출제되는 기타 알고리즘
(이코테 2021 강의 몰아보기) 9. 코딩 테스트에서 자주 출제되는 기타 알고리즘
|
2020-10-10 09:30:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 8. 기타 그래프 이론
(이코테 2021 강의 몰아보기) 8. 기타 그래프 이론
|
2020-10-07 12:15:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 7. 최단 경로 알고리즘
(이코테 2021 강의 몰아보기) 7. 최단 경로 알고리즘
|
2020-10-05 18:30:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 6. 다이나믹 프로그래밍
(이코테 2021 강의 몰아보기) 6. 다이나믹 프로그래밍
|
2020-10-04 10:00:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 5. 이진 탐색
(이코테 2021 강의 몰아보기) 5. 이진 탐색
|
2020-10-03 09:25:06
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 4. 정렬 알고리즘
(이코테 2021 강의 몰아보기) 4. 정렬 알고리즘
|
2020-10-02 09:00:06
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 Meta-Transfer Learning for Zero-Shot Super-Resolution (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
Meta-Transfer Learning for Zero-Shot Super-Resolution (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
|
2020-09-30 17:23:23
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 3. DFS & BFS
(이코테 2021 강의 몰아보기) 3. DFS & BFS
|
2020-09-28 23:40:10
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 2. 그리디 & 구현
(이코테 2021 강의 몰아보기) 2. 그리디 & 구현
|
2020-09-27 21:19:58
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (이코테 2021 강의 몰아보기) 1. 코딩 테스트 출제 경향 분석 및 파이썬 문법 부수기
(이코테 2021 강의 몰아보기) 1. 코딩 테스트 출제 경향 분석 및 파이썬 문법 부수기
|
2020-09-27 00:52:48
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 Shadow Attack - Semantic Adversarial Examples (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
Shadow Attack - Semantic Adversarial Examples (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
|
2020-09-20 15:31:42
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 DETR: End-to-End Object Detection with Transformers (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
DETR: End-to-End Object Detection with Transformers (꼼꼼한 딥러닝 논문 리뷰와 코드 실습)
|
2020-09-19 06:19:31
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Adversarial Patch: 스티커를 붙이기만 하면 인공지능이 망가진다! [NIPS 2017] (인공지능 보안/AI Security)
[꼼꼼한 논문 리뷰] Adversarial Patch: 스티커를 붙이기만 하면 인공지능이 망가진다! [NIPS 2017] (인공지능 보안/AI Security)
|
2020-07-07 23:49:13
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Constructing Unrestricted Adversarial Examples with Generative Models [NIPS 2018] (AI보안)
[꼼꼼한 논문 리뷰] Constructing Unrestricted Adversarial Examples with Generative Models [NIPS 2018] (AI보안)
|
2020-03-30 20:15:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Obfuscated Gradients Give a False Sense of Security [ICML 2018] (인공지능 보안)
[꼼꼼한 논문 리뷰] Obfuscated Gradients Give a False Sense of Security [ICML 2018] (인공지능 보안)
|
2020-03-27 21:30:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Certified Robustness to Adversarial Examples with Differential Privacy [S&P 2019] (AI보안)
[꼼꼼한 논문 리뷰] Certified Robustness to Adversarial Examples with Differential Privacy [S&P 2019] (AI보안)
|
2020-03-19 22:00:18
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Towards Deep Learning Models Resistant to Adversarial Attacks [ICLR 2018] (인공지능 보안)
[꼼꼼한 논문 리뷰] Towards Deep Learning Models Resistant to Adversarial Attacks [ICLR 2018] (인공지능 보안)
|
2020-03-08 21:00:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 자연대수 e(Euler's number) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
자연대수 e(Euler's number) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
|
2020-03-08 16:48:51
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Adversarial Examples Are Not Bugs, They Are Features [NIPS 2019] (인공지능 보안)
[꼼꼼한 논문 리뷰] Adversarial Examples Are Not Bugs, They Are Features [NIPS 2019] (인공지능 보안)
|
2020-03-06 22:31:49
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
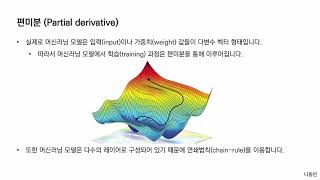 미분과 편미분(Ordinary Derivative & Partial Derivative) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념노트(Mathematics for AI)
미분과 편미분(Ordinary Derivative & Partial Derivative) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념노트(Mathematics for AI)
|
2020-03-01 00:04:58
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Towards Evaluating the Robustness of Neural Networks [S&P 2017] (인공지능 보안/AI Security)
[꼼꼼한 논문 리뷰] Towards Evaluating the Robustness of Neural Networks [S&P 2017] (인공지능 보안/AI Security)
|
2020-02-28 20:04:04
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 볼록 함수(Convex Function) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
볼록 함수(Convex Function) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
|
2020-02-26 08:30:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
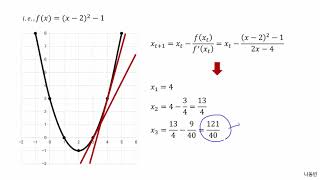 뉴턴 방법(Newton Method) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
뉴턴 방법(Newton Method) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
|
2020-02-24 21:00:07
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 딥 페이크(Deepfakes) 최신 연구 동향 - 가짜 영상 제작과 탐지 기술 정리(Deep Learning for Deepfakes Creation and Detection)
딥 페이크(Deepfakes) 최신 연구 동향 - 가짜 영상 제작과 탐지 기술 정리(Deep Learning for Deepfakes Creation and Detection)
|
2020-02-22 18:01:19
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Explaining and Harnessing Adversarial Examples [ICLR 2015] (인공지능 보안/AI Security)
[꼼꼼한 논문 리뷰] Explaining and Harnessing Adversarial Examples [ICLR 2015] (인공지능 보안/AI Security)
|
2020-02-19 21:00:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 (비전공자) 인공지능 분야 최신 트렌드를 따라가는 방법 및 논문 읽기 조언 [ 개발자의 전화 상담소 ]
(비전공자) 인공지능 분야 최신 트렌드를 따라가는 방법 및 논문 읽기 조언 [ 개발자의 전화 상담소 ]
|
2020-02-02 09:58:17
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 코딩 테스트에선 무엇을 물어보나요? 어떤 언어가 가장 유리한가요? [ 개발자의 전화 상담소 ]
코딩 테스트에선 무엇을 물어보나요? 어떤 언어가 가장 유리한가요? [ 개발자의 전화 상담소 ]
|
2020-01-18 14:53:11
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 네이버 영화 리뷰 데이터 분석 ② 데이터 시각화 [ Python 데이터 분석과 이미지 처리 ]
네이버 영화 리뷰 데이터 분석 ② 데이터 시각화 [ Python 데이터 분석과 이미지 처리 ]
|
2019-10-04 20:00:08
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 네이버 영화 리뷰 데이터 분석 ① 영화 정보 크롤링 [ Python 데이터 분석과 이미지 처리 ]
네이버 영화 리뷰 데이터 분석 ① 영화 정보 크롤링 [ Python 데이터 분석과 이미지 처리 ]
|
2019-10-04 19:30:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 웹 크롤링 [ Python 데이터 분석과 이미지 처리 ] (Web Crawling)
웹 크롤링 [ Python 데이터 분석과 이미지 처리 ] (Web Crawling)
|
2019-10-04 19:00:10
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 Matplotlib 다루기 [ Python 데이터 분석과 이미지 처리 ]
Matplotlib 다루기 [ Python 데이터 분석과 이미지 처리 ]
|
2019-10-03 23:45:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 Matplotlib의 기초 [ Python 데이터 분석과 이미지 처리 ]
Matplotlib의 기초 [ Python 데이터 분석과 이미지 처리 ]
|
2019-10-03 23:00:06
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 Pandas의 활용 [ Python 데이터 분석과 이미지 처리 ]
Pandas의 활용 [ Python 데이터 분석과 이미지 처리 ]
|
2019-10-03 22:30:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 Pandas의 연산과 함수 [ Python 데이터 분석과 이미지 처리 ]
Pandas의 연산과 함수 [ Python 데이터 분석과 이미지 처리 ]
|
2019-10-03 22:00:02
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 Pandas의 기본 사용법 [ Python 데이터 분석과 이미지 처리 ]
Pandas의 기본 사용법 [ Python 데이터 분석과 이미지 처리 ]
|
2019-10-03 21:45:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 중급 Captcha Hacking ⑤ - 해킹 자동화 [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ⑤)
중급 Captcha Hacking ⑤ - 해킹 자동화 [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ⑤)
|
2019-10-02 22:30:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 중급 Captcha Hacking ④ - KNN 모델 학습 [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ④)
중급 Captcha Hacking ④ - KNN 모델 학습 [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ④)
|
2019-10-02 22:00:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 중급 Captcha Hacking ③ - 데이터 정제 [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ③)
중급 Captcha Hacking ③ - 데이터 정제 [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ③)
|
2019-10-02 21:30:04
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 중급 Captcha Hacking ② - 데이터 수집과 분석 [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ②)
중급 Captcha Hacking ② - 데이터 수집과 분석 [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ②)
|
2019-10-02 20:30:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 중급 Captcha Hacking ① - Problem Define [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ①)
중급 Captcha Hacking ① - Problem Define [ Python 데이터 분석과 이미지 처리 ] (CTF Captcha Hacking Project ①)
|
2019-10-02 20:00:10
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 KNN 숫자 인식 예제 [ Python 데이터 분석과 이미지 처리 ]
KNN 숫자 인식 예제 [ Python 데이터 분석과 이미지 처리 ]
|
2019-09-25 22:30:04
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 KNN 알고리즘 [ Python 데이터 분석과 이미지 처리 ] (KNN Algorithm)
KNN 알고리즘 [ Python 데이터 분석과 이미지 처리 ] (KNN Algorithm)
|
2019-09-25 21:30:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 OpenCV Filtering [ Python 데이터 분석과 이미지 처리 ]
OpenCV Filtering [ Python 데이터 분석과 이미지 처리 ]
|
2019-09-22 11:00:00
|
2024-05-16 23:31:00
|
x
|