 HK CODE
HK CODE
|
 참고 리눅스에 아나콘다 설치하기 파트1 리눅스 설치
참고 리눅스에 아나콘다 설치하기 파트1 리눅스 설치
|
2020-05-05 17:59:51
|
2025-02-11 18:05:28
|
x
|
 쉬운코드
쉬운코드
|
 Java에서 SortedMap 정의와 특징 ; HashMap과의 차이 ; 구현체들
Java에서 SortedMap 정의와 특징 ; HashMap과의 차이 ; 구현체들
|
2020-05-05 09:40:19
|
2025-02-13 22:05:28
|
x
|
 데브원영 DVWY
데브원영 DVWY
|
 Confluent의 Kafka cloud서비스를 소개합니다!
Confluent의 Kafka cloud서비스를 소개합니다!
|
2020-05-01 18:39:25
|
2024-05-16 23:31:01
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 [질문답변] 특정 열 기준으로 데이터 합치기 .groupby() .agg()
[질문답변] 특정 열 기준으로 데이터 합치기 .groupby() .agg()
|
2020-04-30 13:00:43
|
2025-05-29 17:05:28
|
x
|
 얄팍한 코딩사전
얄팍한 코딩사전
|
 PWA가 뭔가요? (+모바일 앱의 종류)
PWA가 뭔가요? (+모바일 앱의 종류)
|
2020-04-30 03:17:36
|
2024-05-23 02:05:29
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 04 CSV파일의 구조에 대해 알아보자
04 CSV파일의 구조에 대해 알아보자
|
2020-04-28 23:08:59
|
2025-05-29 17:05:28
|
x
|
 코딩의 신 아샬
코딩의 신 아샬
|
 퀵소트, 머지소트 시간 복잡도 쉽게 외우기
퀵소트, 머지소트 시간 복잡도 쉽게 외우기
|
2020-04-26 21:00:14
|
2024-06-25 00:16:58
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 03 Pycharm에서 git clone하기
03 Pycharm에서 git clone하기
|
2020-04-24 15:58:52
|
2025-05-29 17:05:28
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 02 Python 프로젝트 생성하고 hello출력하기
02 Python 프로젝트 생성하고 hello출력하기
|
2020-04-23 12:57:52
|
2025-05-29 17:05:28
|
x
|
 코딩의 신 아샬
코딩의 신 아샬
|
 함께 일하고 싶은 개발자
함께 일하고 싶은 개발자
|
2020-04-22 23:15:12
|
2024-06-25 00:16:58
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 01 Python Pandas 개발환경 구축하기
01 Python Pandas 개발환경 구축하기
|
2020-04-22 19:29:13
|
2025-05-29 17:05:28
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 JAVA Extends(상속)로 아메리카노 머신과 라떼 머신 만들기
JAVA Extends(상속)로 아메리카노 머신과 라떼 머신 만들기
|
2020-04-19 22:45:10
|
2025-05-29 17:05:28
|
x
|
 코딩의 신 아샬
코딩의 신 아샬
|
 문제-해결-반성 성장 싸이클
문제-해결-반성 성장 싸이클
|
2020-04-19 20:30:12
|
2024-06-25 00:16:58
|
x
|
 가장 쉬운 웹개발 with Boaz
가장 쉬운 웹개발 with Boaz
|
 Browser rendering process 2편 - 렌더링 엔진 동작과정
Browser rendering process 2편 - 렌더링 엔진 동작과정
|
2020-04-17 19:01:27
|
2024-05-16 23:31:04
|
x
|
 가장 쉬운 웹개발 with Boaz
가장 쉬운 웹개발 with Boaz
|
 Browser rendering process 1편 - Browser 구성 요소
Browser rendering process 1편 - Browser 구성 요소
|
2020-04-15 20:49:02
|
2024-05-16 23:31:04
|
x
|
 이노베이션 아카데미
이노베이션 아카데미
|
 [이노베이션아카데미] 방구석 벚꽃놀이 with 이노베이션 아카데미 / 벗꽃맞집 / 랜선나들이 / 사회적거리두기
[이노베이션아카데미] 방구석 벚꽃놀이 with 이노베이션 아카데미 / 벗꽃맞집 / 랜선나들이 / 사회적거리두기
|
2020-04-09 11:23:07
|
2025-06-12 20:05:28
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 [질문답변] Python Pandas(파이썬 판다스)로 피벗테이블 구현하기
[질문답변] Python Pandas(파이썬 판다스)로 피벗테이블 구현하기
|
2020-04-09 10:30:28
|
2025-05-29 17:05:28
|
x
|
 데브원영 DVWY
데브원영 DVWY
|
 개발 생산성을 높여주는 3가지 아이템. 데이터 엔지니어가 선택한 키보드, 마우스, 이어폰!
개발 생산성을 높여주는 3가지 아이템. 데이터 엔지니어가 선택한 키보드, 마우스, 이어폰!
|
2020-04-04 11:22:33
|
2024-05-16 23:31:01
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 토포자를 위한 토비의 스프링3 54~93페이지(Factory) 따라하기
토포자를 위한 토비의 스프링3 54~93페이지(Factory) 따라하기
|
2020-04-04 03:43:01
|
2025-05-29 17:05:28
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Constructing Unrestricted Adversarial Examples with Generative Models [NIPS 2018] (AI보안)
[꼼꼼한 논문 리뷰] Constructing Unrestricted Adversarial Examples with Generative Models [NIPS 2018] (AI보안)
|
2020-03-30 20:15:01
|
2024-05-16 23:31:00
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 파이썬으로 머드게임을 만들어보자 - 01 호감도 올리고 내리기, 돈 올리고 내리기 구현하기
파이썬으로 머드게임을 만들어보자 - 01 호감도 올리고 내리기, 돈 올리고 내리기 구현하기
|
2020-03-29 01:33:21
|
2025-05-29 17:05:28
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Obfuscated Gradients Give a False Sense of Security [ICML 2018] (인공지능 보안)
[꼼꼼한 논문 리뷰] Obfuscated Gradients Give a False Sense of Security [ICML 2018] (인공지능 보안)
|
2020-03-27 21:30:01
|
2024-05-16 23:31:00
|
x
|
 쉬운코드
쉬운코드
|
 Set, HashSet 설명
Set, HashSet 설명
|
2020-03-27 07:46:19
|
2025-02-13 22:05:28
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 [19금]파이썬으로 머드 게임 만들어보자 - 01 프로젝트 생성/대사 구현하기
[19금]파이썬으로 머드 게임 만들어보자 - 01 프로젝트 생성/대사 구현하기
|
2020-03-26 01:14:36
|
2025-05-29 17:05:28
|
x
|
 이노베이션 아카데미
이노베이션 아카데미
|
 [42 SEOUL] EP.02 첫번째 집중교육(라피신) 4주간의 기록, 밀착 영상
[42 SEOUL] EP.02 첫번째 집중교육(라피신) 4주간의 기록, 밀착 영상
|
2020-03-24 16:13:24
|
2025-06-12 20:05:28
|
x
|
 이노베이션 아카데미
이노베이션 아카데미
|
 [42 SEOUL] EP.01 첫번째 집중교육(라피신) 4주간의 기록, 밀착 영상
[42 SEOUL] EP.01 첫번째 집중교육(라피신) 4주간의 기록, 밀착 영상
|
2020-03-23 16:07:14
|
2025-06-12 20:05:28
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 싱가폴 취업 도전 2달 후기
싱가폴 취업 도전 2달 후기
|
2020-03-23 01:19:32
|
2025-05-29 17:05:28
|
x
|
 코딩의 신 아샬
코딩의 신 아샬
|
 Spring Boot 2.2 프로젝트 시작하기
Spring Boot 2.2 프로젝트 시작하기
|
2020-03-22 22:00:17
|
2024-06-25 00:16:58
|
x
|
 코준서
코준서
|
 [Python 기초] 쉘창과 에디터창의 차이를 알아보자
[Python 기초] 쉘창과 에디터창의 차이를 알아보자
|
2020-03-22 17:31:01
|
2024-07-15 20:49:34
|
x
|
 데브원영 DVWY
데브원영 DVWY
|
 AWS에 카프카 클러스터를 설치, 실행해보기!
AWS에 카프카 클러스터를 설치, 실행해보기!
|
2020-03-19 22:14:01
|
2024-05-16 23:31:01
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Certified Robustness to Adversarial Examples with Differential Privacy [S&P 2019] (AI보안)
[꼼꼼한 논문 리뷰] Certified Robustness to Adversarial Examples with Differential Privacy [S&P 2019] (AI보안)
|
2020-03-19 22:00:18
|
2024-05-16 23:31:00
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 최대값 최소값(max, min) 구하는 알고리즘 만들어보고 최적화 하기
최대값 최소값(max, min) 구하는 알고리즘 만들어보고 최적화 하기
|
2020-03-16 09:46:41
|
2025-05-29 17:05:28
|
x
|
 얄팍한 코딩사전
얄팍한 코딩사전
|
 코로나 마스크 재고확인 앱 - 우리동네 마스크
코로나 마스크 재고확인 앱 - 우리동네 마스크
|
2020-03-15 04:10:15
|
2024-05-23 02:05:29
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Towards Deep Learning Models Resistant to Adversarial Attacks [ICLR 2018] (인공지능 보안)
[꼼꼼한 논문 리뷰] Towards Deep Learning Models Resistant to Adversarial Attacks [ICLR 2018] (인공지능 보안)
|
2020-03-08 21:00:00
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 자연대수 e(Euler's number) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
자연대수 e(Euler's number) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
|
2020-03-08 16:48:51
|
2024-05-16 23:31:00
|
x
|
 얄팍한 코딩사전
얄팍한 코딩사전
|
 [코딩만화] Scope가 뭔가요? (feat: let, const, var의 차이)
[코딩만화] Scope가 뭔가요? (feat: let, const, var의 차이)
|
2020-03-07 04:09:37
|
2024-05-23 02:05:29
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Adversarial Examples Are Not Bugs, They Are Features [NIPS 2019] (인공지능 보안)
[꼼꼼한 논문 리뷰] Adversarial Examples Are Not Bugs, They Are Features [NIPS 2019] (인공지능 보안)
|
2020-03-06 22:31:49
|
2024-05-16 23:31:00
|
x
|
 데브멘토(Devmento : Real IT Portal)
데브멘토(Devmento : Real IT Portal)
|
 로보어드바이저를 평가 분석해주는 RA허브 (이기원 대표 인터뷰)
로보어드바이저를 평가 분석해주는 RA허브 (이기원 대표 인터뷰)
|
2020-03-06 08:37:30
|
2024-05-16 23:31:10
|
x
|
 데브멘토(Devmento : Real IT Portal)
데브멘토(Devmento : Real IT Portal)
|
 온오프라인 허리 관리 코칭서비스, 릴리브 (김병준 대표 인터뷰)
온오프라인 허리 관리 코칭서비스, 릴리브 (김병준 대표 인터뷰)
|
2020-03-06 08:34:38
|
2024-05-16 23:31:10
|
x
|
 데브멘토(Devmento : Real IT Portal)
데브멘토(Devmento : Real IT Portal)
|
 기초화장품 창업 이야기: 리메코스, 기초화장품의 본질을 생각하다 (김기원 올리포유코스메틱스 대표)
기초화장품 창업 이야기: 리메코스, 기초화장품의 본질을 생각하다 (김기원 올리포유코스메틱스 대표)
|
2020-03-05 11:15:22
|
2024-05-16 23:31:10
|
x
|
 데브멘토(Devmento : Real IT Portal)
데브멘토(Devmento : Real IT Portal)
|
 초미세 먼지 막으려면 전열교환기 필터 교체해야(정항용 레이노 대표 인터뷰)
초미세 먼지 막으려면 전열교환기 필터 교체해야(정항용 레이노 대표 인터뷰)
|
2020-03-03 17:23:47
|
2024-05-16 23:31:10
|
x
|
 데브멘토(Devmento : Real IT Portal)
데브멘토(Devmento : Real IT Portal)
|
 향기 나는 동전 파스 ‘차크라’로 해외 진출 시동 건다(박재성 무니스튜디오 대표)
향기 나는 동전 파스 ‘차크라’로 해외 진출 시동 건다(박재성 무니스튜디오 대표)
|
2020-03-02 10:53:18
|
2024-05-16 23:31:10
|
x
|
 데브원영 DVWY
데브원영 DVWY
|
 Burrow = 카프카 컨슈머 Lag 모니터링 필수요소
Burrow = 카프카 컨슈머 Lag 모니터링 필수요소
|
2020-03-01 00:16:46
|
2024-05-16 23:31:01
|
x
|
 동빈나
동빈나
|
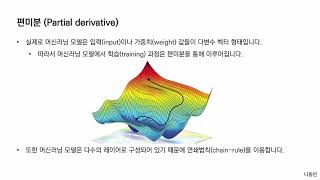 미분과 편미분(Ordinary Derivative & Partial Derivative) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념노트(Mathematics for AI)
미분과 편미분(Ordinary Derivative & Partial Derivative) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념노트(Mathematics for AI)
|
2020-03-01 00:04:58
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Towards Evaluating the Robustness of Neural Networks [S&P 2017] (인공지능 보안/AI Security)
[꼼꼼한 논문 리뷰] Towards Evaluating the Robustness of Neural Networks [S&P 2017] (인공지능 보안/AI Security)
|
2020-02-28 20:04:04
|
2024-05-16 23:31:00
|
x
|
 데브멘토(Devmento : Real IT Portal)
데브멘토(Devmento : Real IT Portal)
|
 목소리 관리하는 O2O 서비스 ‘보이스첵’ (박현선 보이스첵 대표 인터뷰)
목소리 관리하는 O2O 서비스 ‘보이스첵’ (박현선 보이스첵 대표 인터뷰)
|
2020-02-28 14:03:18
|
2024-05-16 23:31:10
|
x
|
 코준서
코준서
|
 [Python] #2 매우 쉽게 풀어낸 tkinter 강의 - 사용하기 쉬운 코드로 GUI프로그램 만들기까지
[Python] #2 매우 쉽게 풀어낸 tkinter 강의 - 사용하기 쉬운 코드로 GUI프로그램 만들기까지
|
2020-02-26 18:19:43
|
2024-07-15 20:49:34
|
x
|
 코준서
코준서
|
 [Python] #1 매우 쉽게 풀어낸 tkinter 강의 - 사용하기 쉬운 코드로 GUI프로그램 만들기까지
[Python] #1 매우 쉽게 풀어낸 tkinter 강의 - 사용하기 쉬운 코드로 GUI프로그램 만들기까지
|
2020-02-26 18:10:32
|
2024-07-15 20:49:34
|
x
|
 동빈나
동빈나
|
 볼록 함수(Convex Function) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
볼록 함수(Convex Function) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
|
2020-02-26 08:30:01
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
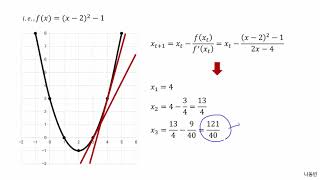 뉴턴 방법(Newton Method) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
뉴턴 방법(Newton Method) | 인공지능 및 컴퓨터 비전을 위한 수학 핵심 개념 노트(Mathematics for AI)
|
2020-02-24 21:00:07
|
2024-05-16 23:31:00
|
x
|
 Hyun-woo Park
Hyun-woo Park
|
 One day dev / 하루개발 – 데이블(dable) 편
One day dev / 하루개발 – 데이블(dable) 편
|
2020-02-22 19:30:02
|
2024-06-09 10:15:24
|
x
|
 동빈나
동빈나
|
 딥 페이크(Deepfakes) 최신 연구 동향 - 가짜 영상 제작과 탐지 기술 정리(Deep Learning for Deepfakes Creation and Detection)
딥 페이크(Deepfakes) 최신 연구 동향 - 가짜 영상 제작과 탐지 기술 정리(Deep Learning for Deepfakes Creation and Detection)
|
2020-02-22 18:01:19
|
2024-05-16 23:31:00
|
x
|
 동빈나
동빈나
|
 [꼼꼼한 논문 리뷰] Explaining and Harnessing Adversarial Examples [ICLR 2015] (인공지능 보안/AI Security)
[꼼꼼한 논문 리뷰] Explaining and Harnessing Adversarial Examples [ICLR 2015] (인공지능 보안/AI Security)
|
2020-02-19 21:00:01
|
2024-05-16 23:31:00
|
x
|
 데브멘토(Devmento : Real IT Portal)
데브멘토(Devmento : Real IT Portal)
|
 삼양그룹 RPA 도입 사례: 삼양그룹 RPA 1차 프로젝트 그 후 (1 of 2) (손현철 과장 발표)
삼양그룹 RPA 도입 사례: 삼양그룹 RPA 1차 프로젝트 그 후 (1 of 2) (손현철 과장 발표)
|
2020-02-19 16:29:15
|
2024-05-16 23:31:10
|
x
|
 데브멘토(Devmento : Real IT Portal)
데브멘토(Devmento : Real IT Portal)
|
 삼양그룹 RPA 도입 사례 : 삼양그룹 RPA 1차 프로젝트 그 후 (2 of 2) (손현철 과장 강연)
삼양그룹 RPA 도입 사례 : 삼양그룹 RPA 1차 프로젝트 그 후 (2 of 2) (손현철 과장 강연)
|
2020-02-19 16:24:54
|
2024-05-16 23:31:10
|
x
|
 쉬운코드
쉬운코드
|
 hash map 설명 (장점, 예제, hash function)
hash map 설명 (장점, 예제, hash function)
|
2020-02-16 22:35:26
|
2025-02-13 22:05:28
|
x
|
 Kyeongrok Kim
Kyeongrok Kim
|
 CSV Parsing and Sorting with Python
CSV Parsing and Sorting with Python
|
2020-02-15 11:55:12
|
2025-05-29 17:05:28
|
x
|
 데브멘토(Devmento : Real IT Portal)
데브멘토(Devmento : Real IT Portal)
|
 마이크로 모빌리티 현황 (전동 킥보드 등 마이크로모빌리티는 왜 증가할까? ), 최영우 울룰로(킥고잉) 대표 발표
마이크로 모빌리티 현황 (전동 킥보드 등 마이크로모빌리티는 왜 증가할까? ), 최영우 울룰로(킥고잉) 대표 발표
|
2020-02-12 09:11:35
|
2024-05-16 23:31:10
|
x
|
 쉬운코드
쉬운코드
|
 배열이 0번째 부터 시작하는 이유
배열이 0번째 부터 시작하는 이유
|
2020-02-10 21:30:02
|
2025-02-13 22:05:28
|
x
|
 쉬운코드
쉬운코드
|
 해설! 10000000 십진수로 바꾸면?!
해설! 10000000 십진수로 바꾸면?!
|
2020-02-07 22:09:58
|
2025-02-13 22:05:28
|
x
|